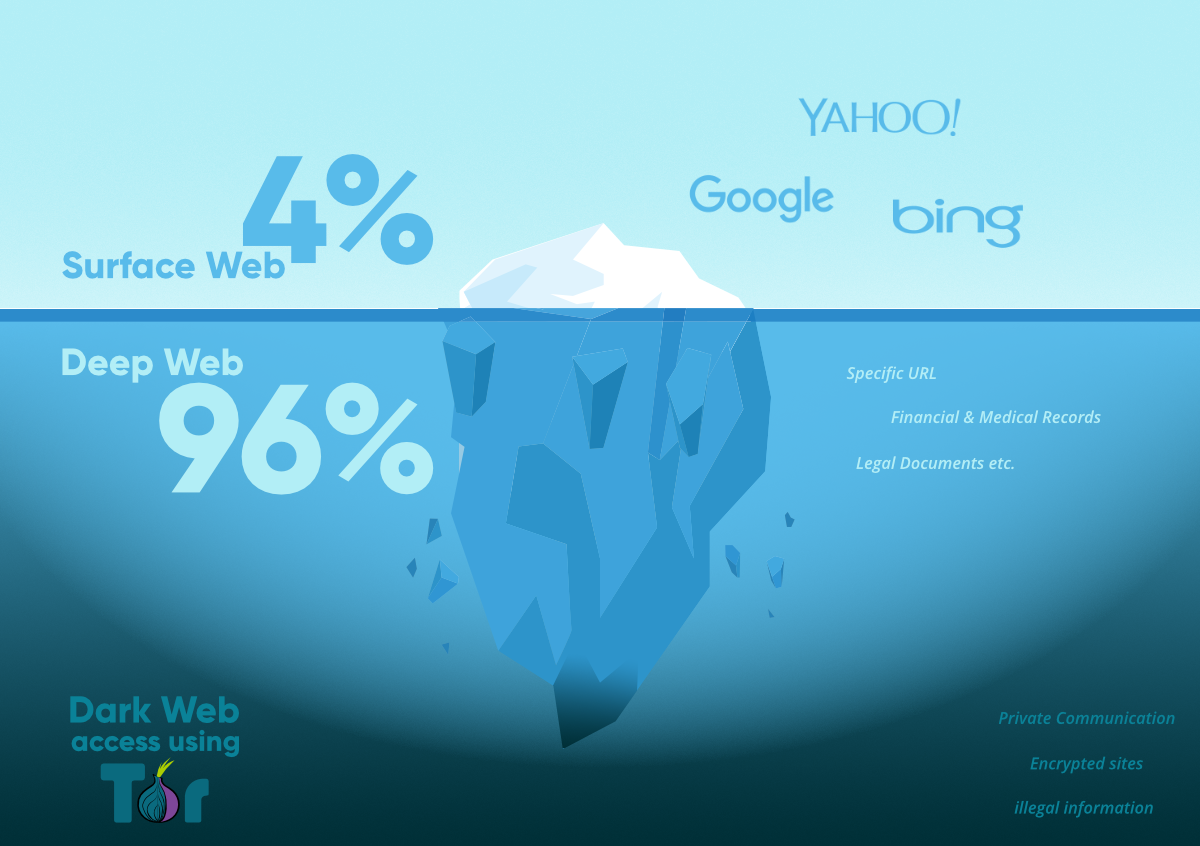
The Deep Web, which is sometimes misunderstood and connected with illegal activity, is a huge and intricate world beyond the reach of traditional search engines. Contrary to common opinion, not all of it is purposefully hidden, and grasping its intricacies is critical to realizing its full potential.
Just Under the Surface:
The familiar surface Web, which is accessible to everyone via search engines, represents only a small portion of the vast online terrain. The majority of the Deep Web stays hidden due to technical problems such as data incompatibility, password-protected sites, and timed-access material. Also, make sure to check out the guide on How to scrub your personal information from Google searches (Safeguarding Your Online Privacy).
Hidden in Plain View:
The Deep Web, which is 400 to 500 times larger than the surface Web, is projected to be 400 to 500 times larger. This hidden store contains vital information ranging from technical databases to medical publications, presenting a challenge to search engines to evolve and bring this material to the surface.
While the Deep Web presents obstacles, its promise is enormous. Consider construction engineers investigating new bridge materials or doctors quickly obtaining the most recent medical research. The technical challenges are significant, but the rewards for solving them could transform how professionals access information.
Darkness Falls from Deep to Dark: Going deeper into the Deep Web leads to the Dark Web, which is properly termed. Here, purposeful hiding is common, and anonymity is essential. In this murky region, criminal activities ranging from illegal commodities to human trafficking thrive. Tor, a specialized software, is required to gain access to this secret area.
Tor, which was originally designed for political dissidents, has become a double-edged weapon. While technology gives privacy, it also makes illicit acts easier. The infamous Silk Road, an online marketplace for illegal goods, shows the dichotomy of technology designed with noble intentions being used for evil.
The Silver Lining in the Darkness:
Aside from its sinister reputation, the Dark Web also houses legal services. Alternative search engines, email services, and political dissident venues can all be found here. The Dark Web is a safe haven for people who value their privacy in an age of surveillance.
However, the Deep Web continues to evolve, testing our ability to absorb its enormous mass of information. As large data becomes an overwhelming problem, improved search algorithms are critical for navigating its depths. Companies that invest in deep Web mining will gain a competitive advantage, while those that rely primarily on the surface Web may struggle to keep up.
Finally, the Deep Web, which reflects both the tremendous potential and the darker elements of human nature, continues to be an intriguing and enigmatic component of the internet. The dynamic environment has the promise of reshaping our society in ways we cannot yet envision as we attempt to understand and utilize its depths.
Here’s a Step-by-Step Guide on how to navigate the Deep Web Safely
Step 1: Understand the Deep Web:
Before diving in, comprehend that the Deep Web is distinct from the surface web, often associated with anonymity and hidden content. Recognize that not all of it is illegal, but caution is crucial.
Step 2: Ensure Anonymity:
If privacy is a concern, use a virtual private network (VPN) to mask your IP address. This helps maintain anonymity and adds an extra layer of security while accessing the Deep Web.
Step 3: Download the Tor Browser:
Tor (The Onion Router) is a specialized browser for accessing the Deep Web. Download it from the official website (https://www.torproject.org/) to ensure a secure connection.
Step 4: Install and Configure Tor:
Follow the installation instructions provided on the Tor website. Configure the browser settings to enhance privacy and security. Ensure that JavaScript is disabled for added protection.
Step 5: Explore Onion Links:
On the Deep Web, websites use “.onion” domains. These are accessible only through the Tor browser. Explore directories and forums that list verified .onion links to find legitimate content.
Step 6: Exercise Caution:
Be wary of suspicious websites and avoid clicking on random links. Stick to well-known and reputable forums to reduce the risk of encountering malicious content.
Step 7: Use Search Engines for the Deep Web:
Specialized search engines like DuckDuckGo or notEvil can help you navigate the Deep Web efficiently. They respect user privacy and provide access to a range of .onion sites.
Step 8: Familiarize Yourself with Deep Web Resources:
The Deep Web hosts a variety of resources, including forums, marketplaces, and information databases. Familiarize yourself with these resources based on your interests, but always exercise caution.
Step 9: Respect Legal and Ethical Boundaries:
While the Deep Web offers anonymity, engaging in illegal activities is against the law. Respect legal and ethical boundaries, and avoid participating in any activities that could compromise your safety or legality.
Step 10: Regularly Update Security Measures:
Keep your Tor browser and VPN software updated to ensure the latest security features. Regularly check for updates on the official websites and follow best practices for online security.
Step 11: Exit Safely:
When finished with your Deep Web activities, close the Tor browser to ensure a secure exit. Remember that your online activities can leave digital footprints, so taking precautions is essential.
Step 12: Stay Informed:
Stay updated on cybersecurity news and best practices for using the Deep Web safely. Being informed helps you adapt to evolving security measures and potential risks associated with the Deep Web.
By following these steps, users can explore the Deep Web with a focus on privacy, security, and ethical considerations. Always prioritize safety and adhere to legal guidelines while navigating this intricate online landscape.






